Chapter 17: Security
Encryption
- Plain text: the original data to be transmitted as a message
- Cipher text: the result of encryption that is transmitted to the recipient
- Digital certificate: An electronic document from a trusted authority that ensures authentication
- Public key: An encryption method produced by a trusted authority that can be used by anyone
- Key widely available that can be used to encrypt message that only owner of the private key can decrypt
- Can be used to decrypt a digital signature, thereby confirming the originator of the message
- Private key - Key needed to decrypt data that has been encrypted by a public key
- Key needed to encrypt data so that it can be decrypted by a public key
- The key used to asymmetric encryption which is not shared
- Encryption: Process of turning plain text into cipher text
Main Security concerns:[^1]
Confidentiality is where only the intended recipient should be able to read or decipher the data; the communication must ensure no interception.
Authenticity is the need to identify who sent the data and verify that the source is legitimate/genuine.
Integrity is that data should reach its destination without any changes.
Non-repudiation is that neither the sender nor the recipient should be able to deny that they were part of the data transmission which just took place.
Availability: Nothing should happen to prevent the receiver from receiving the transmission
[^1]: These five words appears constantly in mark schemes; so just write about them if you have no idea about the question
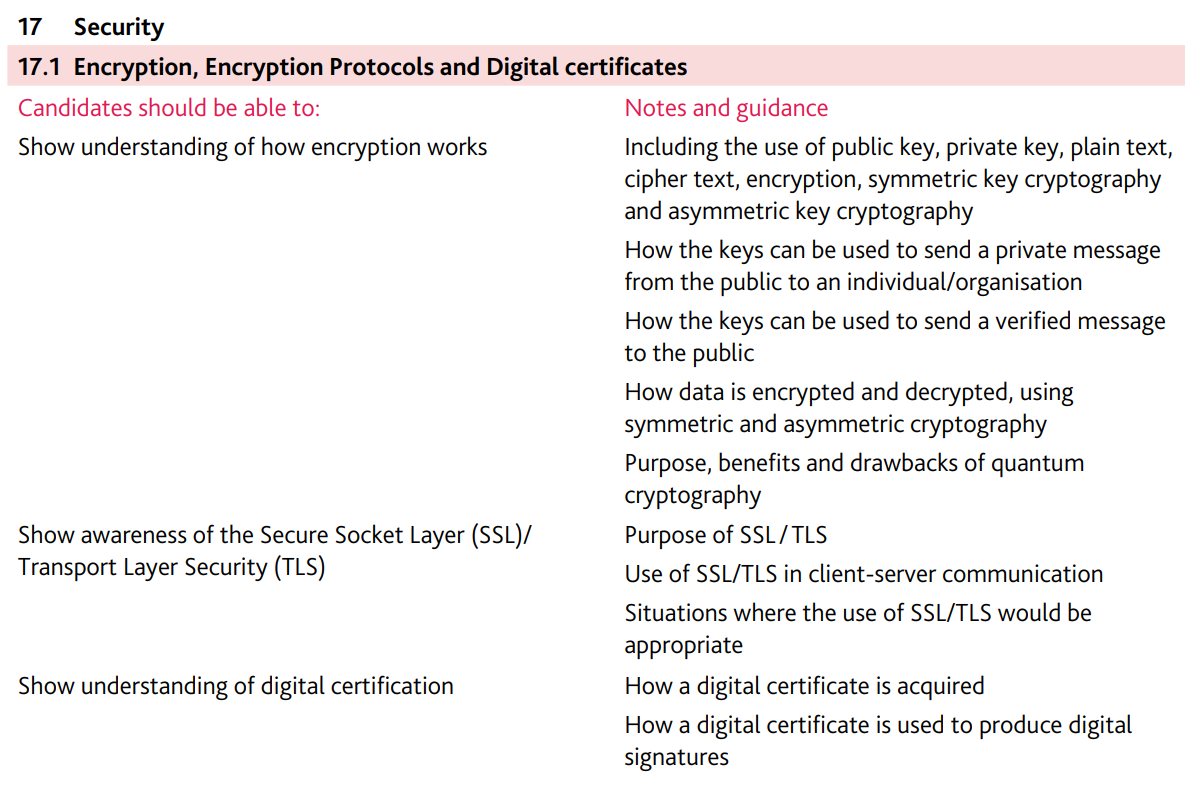
Asymmetric key cryptography
Encryption that uses public keys and private keys
- Asymmetric encryption uses a matching pair of keys
- A public key (available to everyone)
- Receiver’s public key used to encrypting the message before it is sent
- A private key (only known to the owner of the key)
- Receiver’s private key to decrypt the message after it has been received
Benefits:
- Increased message security as one key is private
- Allow message authentication
- Allows non-repudiation
- Detects tampering(篡改)
Symmetric key cryptography
A single key is used for both encryption and decryption
Drawbacks:
- Key has to be exchanged securely
- Once, compromised, the key can be used to decrypt both sent and received messages
- Cannot ensure non-repudiation
| Public key & Private key | |
|---|---|
| Similarity | - Both used in asymmetric encryption - As a pair of key is required - One is used to encrypt the data and the other is used to decrypt the data - Both hashing algorithms |
| Difference | - Private key is only known to the owner of the key pair - The public key can be distributed to anyone - When message is sent to the owner of the public key, they are encrypted with the public key - So they could be only decrypted with owner’s private key - Message digest are encrypted with the private key to form a digital signature - Messages are encrypted with the public key of the receiver |
Quantum Cryptography/ Quantum key distribution(QKD)
Purpose
- Use quantum mechanics to facilitate the secure transmission of encryption keys
Benefits:
- Any eavesdropping can be identified
- Integrity of the key once transferred can be guaranteed; cannot copied or decrypt at a later date
- Longer/more secure keys can be exchanged
Drawbacks:
- It requires a dedicated line and a specialist hardware, which can be expensive to implement initially
- It still has a limited range
- It is possible for polarisation of light to be altered while travelling down fibre obtic cables
- Due to the inherent security system generated by quantum cryptography, terrorists and other criminals can use the technology to hide their activities from government law enforces
Past paper questions
Secure socket layer(SSL) and Transport layer security(TLS)
Purpose:
- The SSL & TLS provide communication security over the internet/network
- … they provide encryption
- They enable two parties to identify and authenticate each other
- … and communicate with confidentiality and integrity
Situations where the use of SSL/TLS would be appropriate:
- Online banking and all online financial transactions
- Online shopping/commerce
- Sending software to a restricted list of users
- Sending and receiving emails
- Using cloud storage facilities
- Intranet, extranet, and internet
- Using virtual private networks (VPNs)
- Using Voice over Internet Protocol (VOIP) for video and audio chatting over the internet
- Using instant messaging
- Making use of a social networking site
Difference between SSL and TLS
- It is possible to extend TLS by adding new authentication methods
- TLS can make use of session caching which improves the overall performance of computer compared to using SSL
- TLS separate handshaking process from record protocol layer
SSL
- Encrypts the data when the user logs onto a website
- Only the client’s computer and the web server are able to make sense of what is being transmitted
- Data compression: reducing the amount of data being transmitted
- Data integrity checks
TLS
- Record layer can be used with or without encryption; it contains the data being transmitted over the internet
- Handshake protocol permits the web server and client to authenticate each other and to make use of encryption algorithms (a secure session between the client and server is then established)
- Cipher suite
- Session caching avoids the need to utilize computer time during each TLS connection; TLS can either initiate new session or resume existing session; the latter can save considerable computer time
- A protocol with two layers
- Handshake and Record layers
- A TLS/digital/public key certificate is used for authentication
- Handshake uses asymmetric cryptography
- To generate agreed paramters
- Establish a shared session key
- The shared session key provides symmetric cryptography for sending a receiving data(record layer)
- At the end of the session, all the paramters, keys, etc. are erased
Situations where the use of TLS would be appropriate:
- Browser accessing secure websites. eg: bank transaction
- VPNs - Virtual private networks
- VOIP - Voice over Internet Protocols
Describe the type of activity where SSL or TLS would be used
- A client
- … is accessing a website
- … and needs to communicate with the website
- … without the possibility that the communication being intercepted or scrutinized by an unauthorized party
- … because sensitive data is being transferred
Past paper questions
1.
Problems that SSL/TLS helps to overcome:
- Security: alteration of transmitted message
- Privacy: only intended receiver can view data
- Authentication: trust in other party
Security parameters agreed during the handshake process:
- Which protocol will be used
- There are a number of different versions of the two protocol
- Session ID
- Uniquely identifies a related series of message between the client and server
- Session type
- Reusable or not
- Encryption method
- public/private key to be used
- Authentication method
- Use of digital certificates
- Compression
- … methods to be used
3.
Explain how SSL/TLS protocols are used when a client-server communication is initiated.
- An SSL/TLS connection is initiated by an application
- … which becomes the client
- The application which receives the connection becomes the server
- Every new session begins with a handshake (as defined in the SSL/TLS protocols)
- The client requests the digital certificate from the server // The server sends the digital certificate to the client
- The client verifies the server’s digital certificate
- And the obtains the server’s public key
- The encryption algorithms are agreed
- The symmetric
- … session keys are generated
4.
The sequence of steps describes what happens when setting up a secure connection using Secure Socket Layer (SSL)[^2]
- Browser requests that the server identifies itself
- Server sends a copy of its SSL Certificate and its public key
- Browser checks the certificate against a list of trusted certificate authorities
- If the browser trusts the certificate, it creates, encrypts and sends the server a symmetric session key using a server’s public key
- Server decrypts the symmetric session key using its private key
- Server sends the browser an acknowledgment, encrypted with the session key.
- Server and browser now encrypt all transmitted data with the session key
[^2]: Q4 is a more detailed version of Q3
Digital certification📃
Digital certificate
An electrical document used to prove the identity of a website or individual. It contains a public key and information identifying the website owner or individual, issued by a Certificate Authority (CA)
Contains:
Serial number
Hashing algorithm
- To produce the message digest
Public key
- To decrypt/encrypt data
Dates valid
Name of organization
Signature to verify it came from the issuers
Name of issuer
Purpose of the public key
Thumb print/finger print algorithm
This is the hash function used to produce a message digest
CA digital certificate
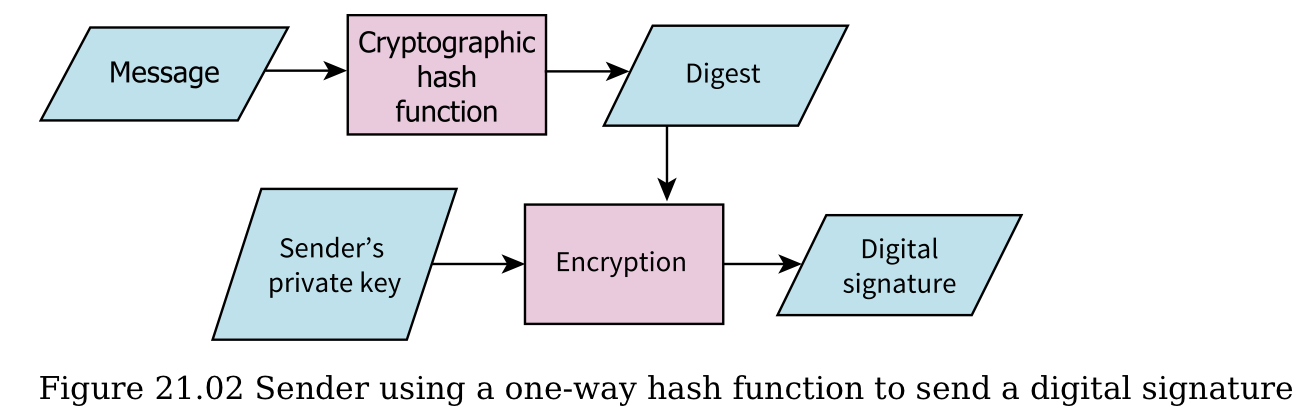
Explain how asymmetric encryption uses the content of the digital certificate to ensure that the message has not been altered during transmission
- A’s message is encrypted using B’s public key
- A’s hashing algorithm is used on the message to produce the message digest
- The message digest is then encrypted with A’s private key to provide a digital signature
- Both the encrypted message and the digital signature is sent
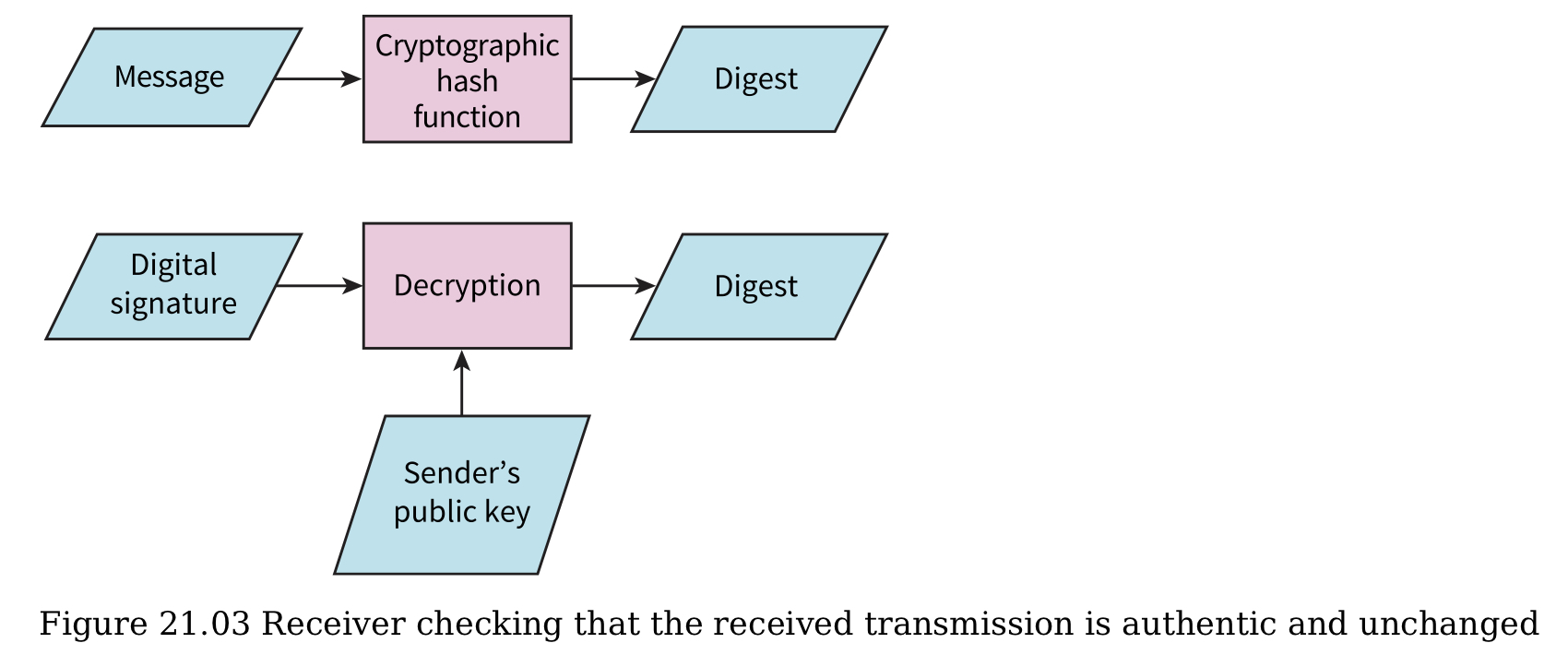
- The message is decrypted with B’s private key
- A’s digital signature is decrypted with A’s public key to obtain the message digest
- A’s hashing algorithm recreates the message digest from the decrypted message
- The two message digests are compared, if they are the same then the message should be authentic / has not been tampered.
Explain the process organisation follows to obtain digital certificate
- Appied to an issuing Certificate Authority (CA)
- With some proof of identity
- Eg: name of organisation, address of organization
- So their identity can be checked by the organisational registration authority
- So that the digital certificate will only be issued to a trusted organization
Digital signature✒
Electronic way of validating the authenticity of digital documents; that is, making sure they have not been tampered with during transmission and also proof that a document was sent by a known user
Purpose:
- To ensure a document is authentic // came from a trusted source
- To ensure a document has not benn altered during transmission
- Non-repudiation
| Digital certificate & digital signature | |
|---|---|
| Similarities: | Both used for authentication Both are unique to the owner/subject Include / use owner’s public key Include / make use of hashing algorithm |
| Differences: | Certificate obtained from issuing authority Signature created from a message Certificate provides authentication of owner Signature used to authenticate message that are sent by the owner Certificate remains unchanged whilst it is valid New signature created for every message Only certificate provide extra information Only signature make use of a private key |
Past paper questions
1.
Give two uses where the encrypted message digest is advisable:
- Financial transaction
- Legal document
- Software distribution
A user downloads software from the internet.
State what should be part of the download to provide proof that the software is authentic
- Digital signature
Describe the process for ensuring that the software is both authentic and has not been altered
Software is put through a hashing algorithm to produce a digest
The digest is encrypted using the private key to produce a digital signature
The software is sent along with the digital signature
The receiver is in possession of the sender’s public key
The received digital signature is decrypted with sender’s public key to produce the digest
The received software is hashed to produce another digest
Compare if the two digests are equal
If so, then the software is authentic and has not been altered